Hipaa Compliant Voip Guide: Secure Communication in 2025
Discover how to select and implement HIPAA compliant VoIP in 2025. Learn best practices, security features, and top vendors for secure healthcare communication.
Redaction
08/11/2025, 12:30:00The healthcare industry faces a growing wave of cyber threats, making secure communication a top priority for every organization. With remote care and digital health records now the norm, hospitals and clinics must ensure that every voice call and message meets HIPAA standards in 2025.
Choosing the right hipaa compliant voip solution is more important than ever. Healthcare providers, IT managers, and compliance officers need a clear path to secure, compliant communication - one that protects patient privacy and supports modern care delivery.
This comprehensive guide will walk you through the essentials of hipaa compliant voip. You'll learn how to select, implement, and maintain VoIP systems that safeguard sensitive data and keep your organization in line with the latest regulations.
We'll cover everything you need to know: HIPAA requirements, VoIP technology basics, compliance steps, core security features, vendor selection tips, and the future trends shaping secure healthcare communication.
Understanding HIPAA Compliance for VoIP in 2025
The Health Insurance Portability and Accountability Act (HIPAA) is the foundation of patient data protection in the United States. Its rules directly affect how healthcare organizations use communication technologies, especially as digital transformation accelerates. By 2025, the requirements for hipaa compliant voip systems have become more rigorous, reflecting the growing risks of cyber threats targeting voice communications.
HIPAA consists of three major rules: the Privacy Rule, the Security Rule, and the Breach Notification Rule. The Privacy Rule regulates who can access protected health information (PHI). The Security Rule sets standards for safeguarding electronic PHI (ePHI), focusing on administrative, physical, and technical safeguards. The Breach Notification Rule mandates that organizations report any unauthorized disclosures of PHI, including those resulting from compromised communication systems.
For a VoIP system to be considered a hipaa compliant voip solution, it must implement several core safeguards. Encryption is essential, ensuring that voice data remains confidential both in transit and at rest. Access controls restrict system use to authorized personnel, while audit trails log all access and administrative actions. Data integrity measures, such as checksums and secure storage, help prevent tampering or accidental loss of sensitive information.
Regulatory expectations for hipaa compliant voip are evolving. In 2025, new guidance from the Department of Health and Human Services (HHS) emphasizes the need for end-to-end encryption, robust authentication, and continuous risk assessment. For a detailed summary of these updates, see the New HIPAA Security Rule NPRM Overview, which outlines enhanced cybersecurity measures that specifically impact VoIP systems. Recent enforcement actions show regulators are scrutinizing the use of cloud-based telephony and the security of remote communications more closely than ever.
Types of data covered under hipaa compliant voip requirements include any voice communication that contains PHI. This encompasses not only live calls but also voicemails, call recordings, and even call transcripts. Each of these must be encrypted, stored securely, and accessed only by authorized users. Organizations must ensure that these communications are never transmitted or stored on unsecured devices or networks.
Healthcare providers often encounter challenges when implementing hipaa compliant voip. Common pitfalls include misconfigured security settings, unprotected endpoints such as mobile phones or laptops, and the use of third-party vendors without proper due diligence. Cloud-based VoIP solutions introduce additional vulnerabilities if not properly secured, including risks of data interception or unauthorized access by service providers.
Real-world cases highlight the consequences of non-compliance. In 2023, a mid-sized hospital faced a $1.2 million penalty after an unencrypted call recording system exposed patient information. Another provider suffered a breach when a third-party VoIP vendor failed to implement adequate access controls. According to the latest data, approximately 30% of healthcare data breaches in 2024 involved communication systems, with the average cost of a HIPAA violation reaching $480,000.
| Case/Statistic | Description | Year |
|---|---|---|
| Hospital call recording breach | $1.2M penalty due to unencrypted call data | 2023 |
| VoIP vendor access control failure | Patient PHI exposed, regulatory investigation | 2024 |
| % breaches via communication systems | 30% of healthcare data breaches | 2024 |
| Avg. HIPAA violation cost | $480,000 per incident | 2024 |
To mitigate these risks, it is crucial to sign a Business Associate Agreement (BAA) with any VoIP vendor that handles PHI. A BAA legally binds the vendor to comply with HIPAA safeguards, ensuring shared responsibility for patient data protection.
In summary, understanding hipaa compliant voip requirements in 2025 is vital for healthcare organizations seeking to protect patient privacy and avoid costly penalties. By focusing on encryption, access controls, regulatory updates, and vendor agreements, providers can build a secure communication environment that meets both current and future compliance standards.
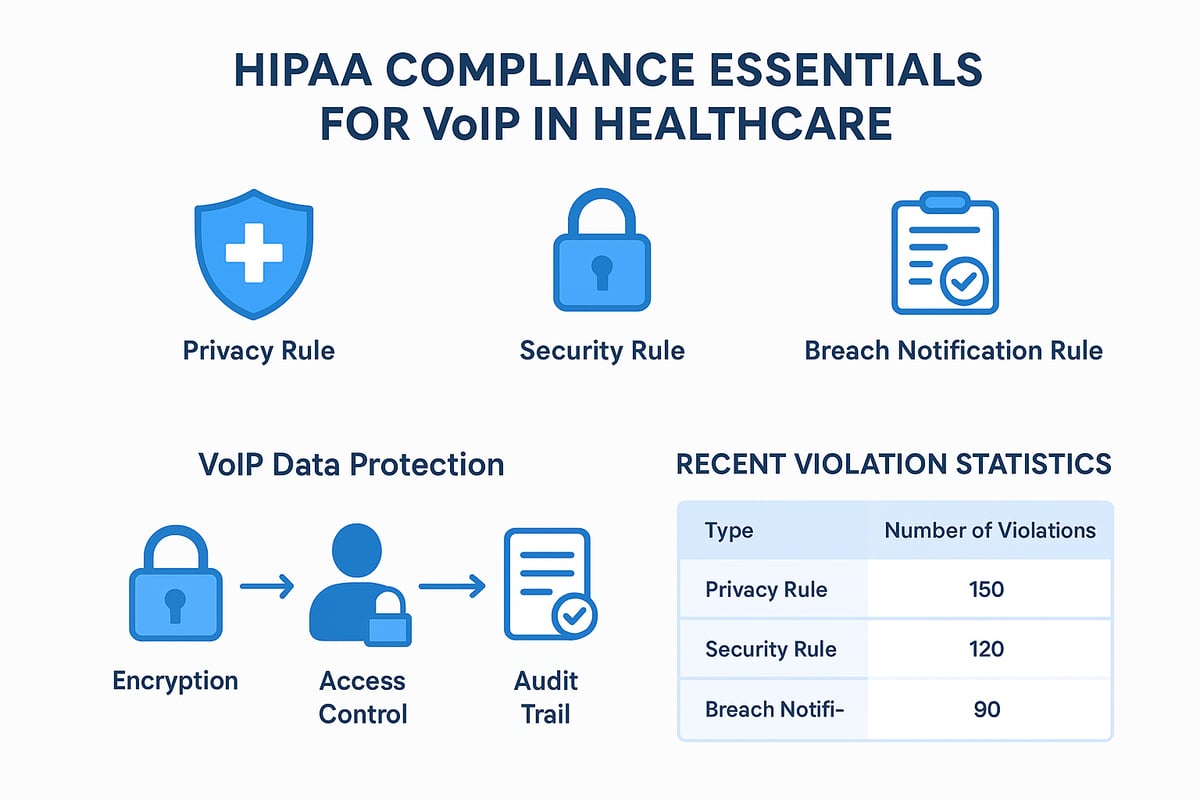
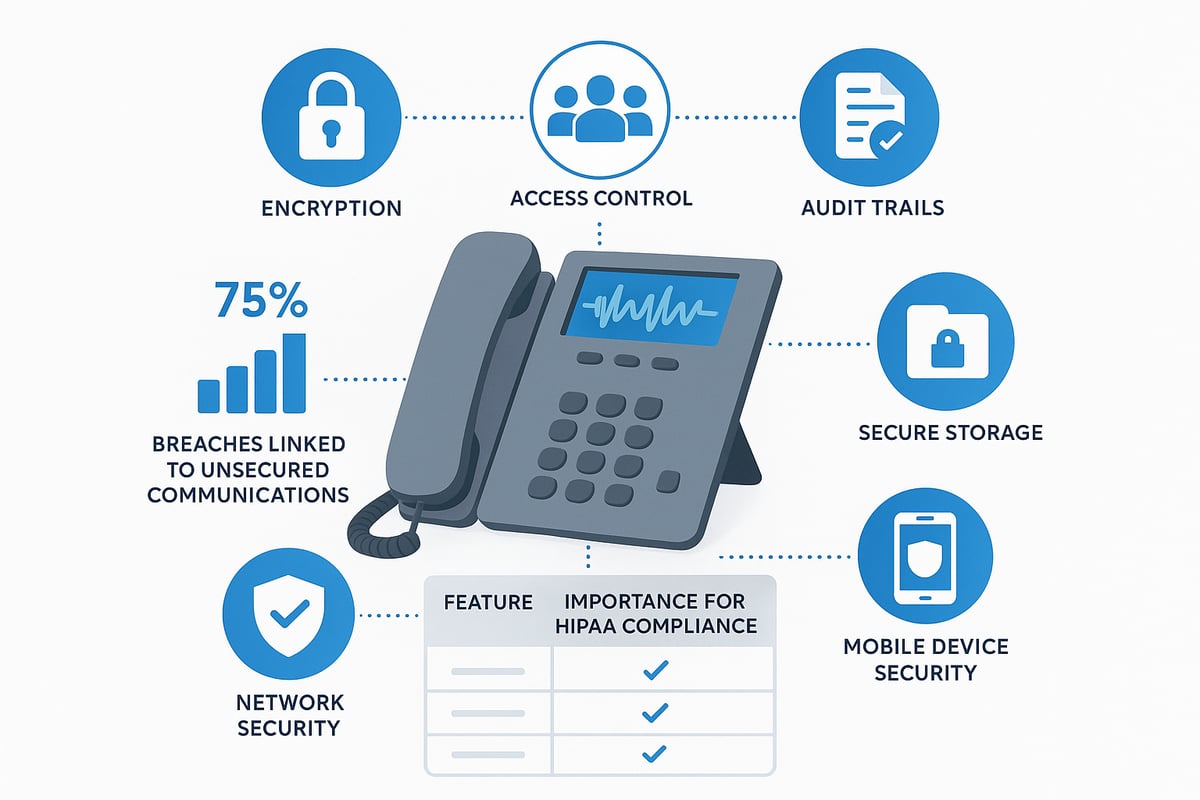
Core Security Features of HIPAA Compliant VoIP Systems
Securing patient data is at the heart of hipaa compliant voip in healthcare. Each security feature serves as a critical barrier against unauthorized access, ensuring seamless communication while protecting sensitive information.
End-to-End Encryption: Protocols and Importance
End-to-end encryption is the foundation of hipaa compliant voip. This security method ensures that voice data is encrypted from the moment it leaves the sender’s device until it reaches the recipient. Protocols such as Secure Real-Time Transport Protocol (SRTP) for media streams and Transport Layer Security (TLS) for signaling are standard.
These protocols prevent eavesdropping and interception during transmission. Without encryption, sensitive patient information is vulnerable to cybercriminals. HIPAA requires that all electronic protected health information (ePHI), including voice calls and voicemails, be encrypted both in transit and at rest. For a deeper dive into advanced protocols and real-world enterprise implementations, consider reading about Enterprise VoIP Security Features.
Robust Authentication and Access Control
Authentication and access control are vital for any hipaa compliant voip system. Role-based permissions ensure only authorized staff can access specific functions or data. Multi-factor authentication (MFA) adds another layer of protection, requiring users to verify their identity through multiple methods.
Effective user management is also essential. Regularly updating user roles and promptly removing access for departing employees helps reduce insider threats. These controls minimize the risk of unauthorized access to patient communications and support ongoing HIPAA compliance.
Comprehensive Audit Trails and Monitoring
Audit trails provide detailed records of all activity within a hipaa compliant voip system. This includes call logs, access attempts, administrative changes, and more. Monitoring tools track these activities in real time, enabling quick detection of suspicious behavior.
Audit trails are critical for compliance investigations and breach response. They help healthcare organizations prove that proper safeguards were in place if an incident occurs. HIPAA mandates that organizations retain these logs for a specified period, supporting transparency and accountability.
Secure Storage of VoIP Call Data
Storing call data securely is another core requirement for hipaa compliant voip. Voicemails, call recordings, and transcripts must be encrypted and stored in compliance with HIPAA retention policies. Access to stored data should be tightly controlled and monitored.
Retention policies should align with both regulatory requirements and organizational needs. Automatic deletion after a set period helps minimize risk. Regular reviews of storage systems and permissions ensure ongoing protection of sensitive information.
Network Security for VoIP
Network security forms the backbone of any hipaa compliant voip deployment. Firewalls and intrusion detection systems protect VoIP traffic from external threats. Segmentation of VoIP traffic from other network data limits exposure in case of a breach.
Secure network configuration, such as using dedicated VLANs and strict firewall rules, reduces vulnerabilities. Regular vulnerability assessments and timely patching of network devices are key best practices. These steps are crucial for maintaining HIPAA compliance in a dynamic threat landscape.
Mobile Device Security in Healthcare
Mobile device security is essential as clinicians increasingly use smartphones and tablets for communication. A hipaa compliant voip solution must support secure mobile apps, enforce encryption, and manage device access.
Bring Your Own Device (BYOD) policies introduce risks if not properly managed. Organizations should require device-level encryption, remote wipe capabilities, and strong authentication on all devices accessing ePHI. Regular security training for staff using mobile VoIP apps further reduces the risk of breaches.
Comparing VoIP Security: Example and Statistics
The difference between VoIP systems with and without robust security features is significant. Consider the following comparison:
| Security Feature | Non-Compliant VoIP | HIPAA Compliant VoIP |
|---|---|---|
| Encryption | No | Yes |
| Access Control | Basic | Role-Based, MFA |
| Audit Trails | Limited | Comprehensive |
| Secure Storage | Unencrypted | Encrypted |
| Network Security | Minimal | Firewalls, IDS |
Recent industry data shows that over 30% of healthcare data breaches involve communication systems. The average cost of a HIPAA violation now exceeds $400,000 per incident. Adopting hipaa compliant voip significantly reduces these risks and protects both patients and organizations.
Step-by-Step Guide to Implementing HIPAA Compliant VoIP
Adopting a hipaa compliant voip system requires careful planning, technical precision, and ongoing diligence. This guide breaks the process into manageable steps so you can secure patient data and meet regulatory obligations with confidence.
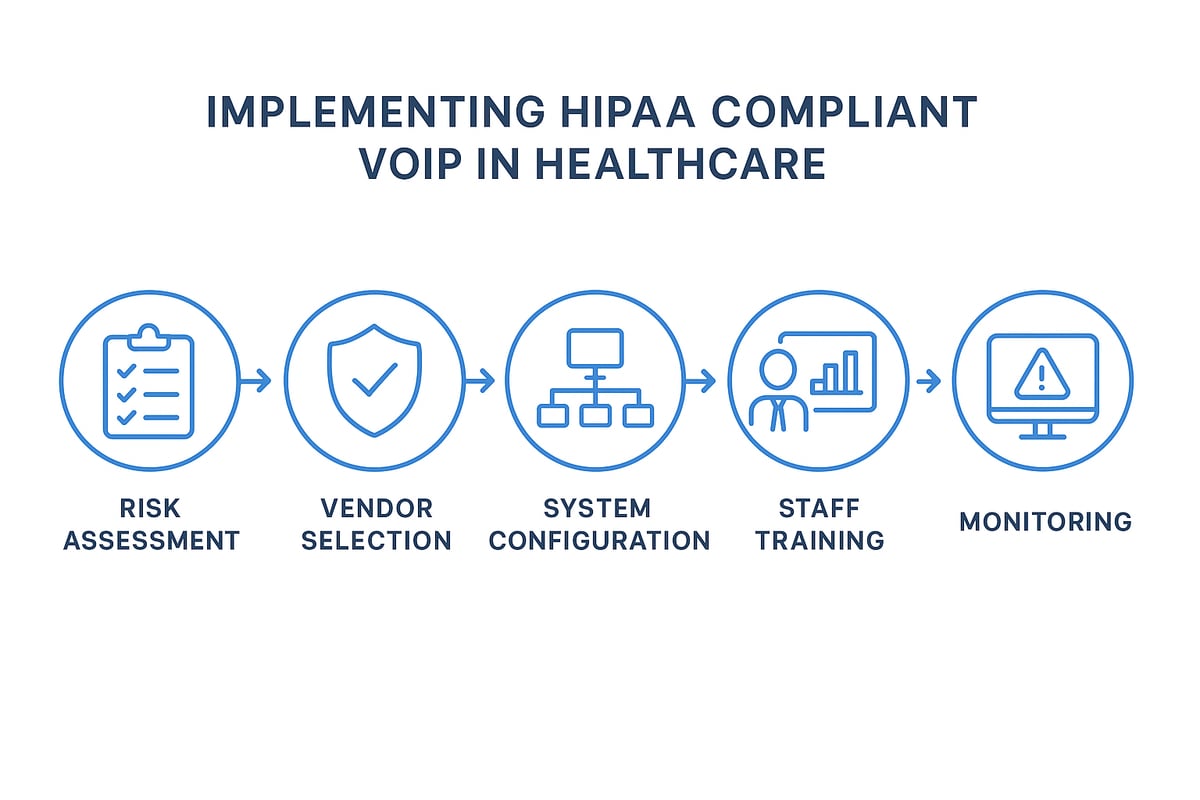
Assessing Organizational Needs and Risks
The first step in deploying a hipaa compliant voip solution is to map out how your organization handles patient information in voice communications. Identify every workflow where Protected Health Information (PHI) is exchanged, such as phone consultations, appointment reminders, and voicemails.
Next, evaluate your current telephony setup for compliance gaps. Are calls encrypted? Who can access voicemail recordings? Involve stakeholders from compliance, IT, and clinical teams to ensure a holistic view.
Use a risk assessment checklist like the one below:
| Risk Area | Questions to Ask | Status |
|---|---|---|
| Data Flow | Where does PHI travel during calls? | |
| Device Security | Are all endpoints secured and patched? | |
| Access Controls | Who can access call recordings and voicemails? | |
| Third-Party Risks | Are vendors HIPAA compliant and under a BAA? |
Document all findings and prioritize remediation. This groundwork is essential for a robust hipaa compliant voip deployment.
Selecting the Right HIPAA Compliant VoIP Vendor
Choosing a hipaa compliant voip provider is a pivotal decision. Look for vendors with proven HIPAA compliance, security certifications, and willingness to sign a Business Associate Agreement (BAA). Transparency in documentation and accessible support channels are must-haves.
Evaluate offerings using these criteria:
- Encryption standards and secure protocols
- Availability of BAAs
- Integration with EHR and healthcare apps
- Uptime guarantees and support responsiveness
Compare leading solutions using resources like the Best VoIP Solutions for Businesses guide to ensure your vendor meets all necessary requirements. Avoid vendors that lack legal agreements or can't demonstrate compliance.
Configuring and Securing the VoIP System
Once you've selected a hipaa compliant voip provider, system configuration is your next priority. Enable end-to-end encryption using protocols such as SRTP and TLS. Set up user authentication with strong passwords and multi-factor authentication.
Integrate your VoIP system with electronic health records (EHR) and secure messaging platforms to streamline workflows. Network configuration should include dedicated VLANs, strict firewall rules, and endpoint security measures.
For compliance, ensure that voicemail and call recordings are stored securely, with access limited to authorized users. Here's a sample secure configuration checklist:
- Enable SRTP and TLS for all voice traffic
- Require MFA for all admin accounts
- Restrict access to call recordings by role
- Patch all VoIP software regularly
- Document configuration changes
Regularly review and update these settings as threats and regulations evolve.
Training Staff and Maintaining Compliance
Even the best hipaa compliant voip system is only as secure as its users. Provide training to all staff on HIPAA rules and secure VoIP usage. Cover topics like recognizing phishing attempts, using strong passwords, and reporting suspicious activity.
Schedule regular refresher courses and simulated breach drills to reinforce best practices. Monitor user activity and audit logs to catch potential violations early. Keep thorough documentation of all training, incidents, and compliance efforts to demonstrate accountability.
Ongoing Monitoring and Incident Response
Continuous vigilance is key to maintaining a hipaa compliant voip environment. Implement automated monitoring tools to detect unusual patterns, such as repeated failed login attempts or unauthorized access to call data.
Set up real-time alerts for suspicious activity and establish a clear incident response plan for VoIP-related breaches. This plan should outline roles, communication protocols, and steps for mitigating damage.
Conduct regular compliance audits and risk assessments to ensure your system remains secure. By prioritizing ongoing monitoring, you create a proactive defense against evolving threats and ensure your hipaa compliant voip investment delivers lasting protection.
Evaluating and Comparing HIPAA Compliant VoIP Solutions
Choosing the right hipaa compliant voip solution demands careful evaluation. Healthcare organizations face unique challenges, so you need to weigh security, compliance, and operational needs. Understanding the essential criteria will help you make an informed decision that protects patient data and ensures regulatory compliance.
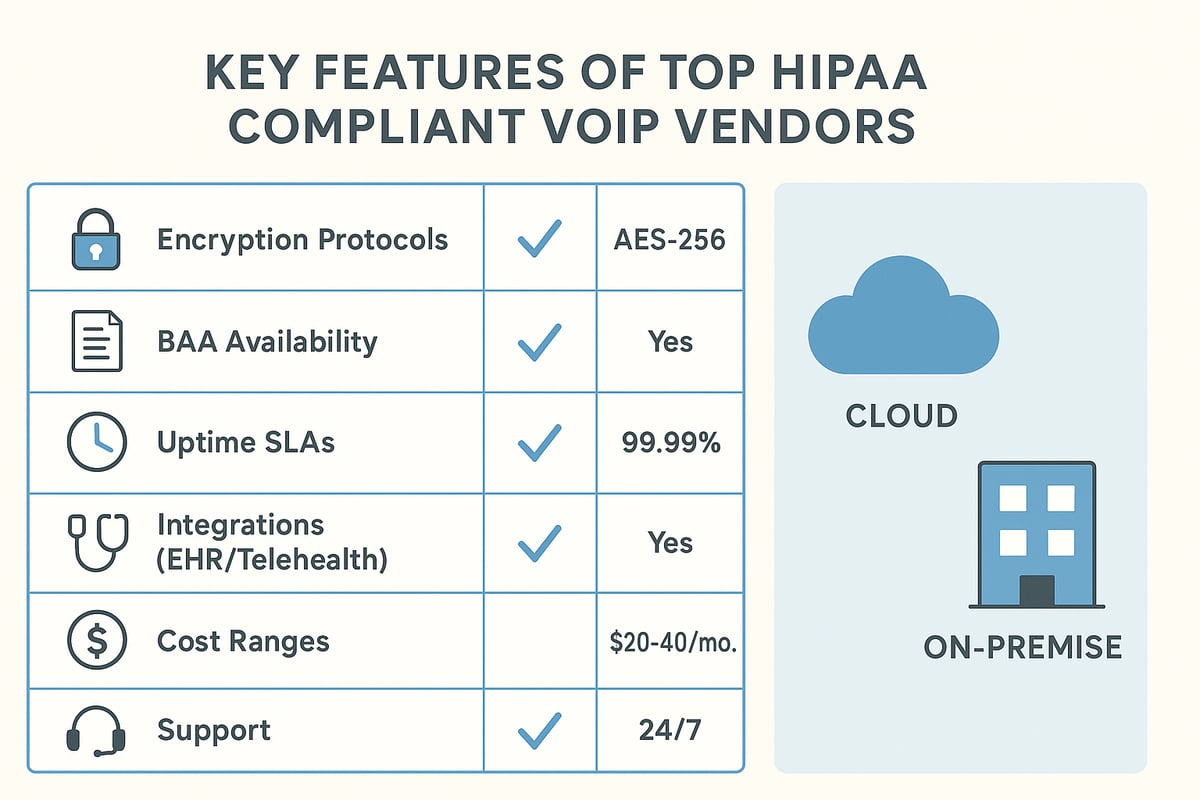
Key Features to Compare
When evaluating hipaa compliant voip providers, focus on core security and compliance features. Look for end-to-end encryption, signed Business Associate Agreements (BAAs), and robust uptime Service Level Agreements (SLAs).
Consider integrations with your electronic health record (EHR) system and telehealth platforms. Scalability is vital, as your communication needs may grow. Responsive support and clear documentation are also essential for ongoing compliance.
- Encryption (SRTP, TLS)
- BAA availability
- Uptime guarantees (99.99%+)
- EHR/telehealth integrations
- Scalability and support
On-Premise vs. Cloud-Based Solutions
Deciding between on-premise and cloud-based hipaa compliant voip systems requires understanding your organization's resources and risk tolerance. On-premise solutions provide direct control over data and infrastructure, but involve higher upfront costs and ongoing maintenance.
Cloud-based systems offer flexibility, easier updates, and predictable pricing. They are often faster to deploy and scale. However, ensure the vendor provides data residency options and strong security controls. For example, CloudTalk Phone Service Overview details a leading cloud-based provider with healthcare-focused features.
Evaluate which model best aligns with your compliance posture and IT capabilities.
Integration and Cost Analysis
Integration with EHR, telehealth, and collaboration tools is a non-negotiable for modern hipaa compliant voip deployments. Seamless interoperability boosts clinical productivity and reduces manual errors.
Cost analysis should cover more than upfront expenses. Factor in ongoing subscription fees, support, training, and any add-ons. The hidden costs of non-compliance, such as fines or breach remediation, can far exceed initial investments. Always request transparent pricing and review contract terms before committing.
- Upfront vs. subscription costs
- Training and support expenses
- Compliance-related penalties
Comparing Top Vendors
Comparing hipaa compliant voip vendors side-by-side helps clarify your options. Use a structured table to assess feature sets, compliance posture, and market reputation.
| Vendor | Encryption | BAA | Uptime SLA | EHR Integration | Cloud/On-Prem | Support |
|---|---|---|---|---|---|---|
| Vendor A | Yes | Yes | 99.99% | Yes | Cloud | 24/7 |
| Vendor B | Yes | Yes | 99.95% | Limited | On-Prem | 8/5 |
| Vendor C | Yes | Yes | 99.99% | Yes | Cloud | 24/7 |
For a detailed breakdown of leading options, review this HIPAA-Compliant VoIP Providers Comparison, which covers features, pricing, and healthcare suitability.
Common Pitfalls and Closing
Avoid common pitfalls when selecting a hipaa compliant voip vendor, such as neglecting to secure a BAA, overlooking integration needs, or underestimating ongoing support requirements. Rely on vendor transparency, peer reviews, and third-party validations to guide your decision.
A strategic evaluation ensures your VoIP system remains both secure and compliant, supporting your organization’s mission to protect patient information.
Future Trends: The Evolution of Secure VoIP in Healthcare
The landscape of hipaa compliant voip is transforming as healthcare organizations face new security challenges and technological advancements. Looking ahead to 2025 and beyond, several trends will define the future of secure healthcare communication.
AI and Automation in HIPAA Compliant VoIP
Artificial intelligence is revolutionizing hipaa compliant voip by automating compliance monitoring and enhancing security. AI-powered call analytics can scan conversations for sensitive information and alert compliance teams to potential risks in real time. Automated transcription services, when securely encrypted and stored, streamline documentation while preserving privacy.
Voice biometrics is another innovation, enabling secure authentication for clinicians and patients. This reduces the risk of unauthorized access to protected health information. For example, AI-driven compliance alerts can notify administrators of unusual call patterns or attempted data breaches.
Many leading vendors now offer AI features within hipaa compliant voip platforms, making it easier to track user activity and maintain audit trails. Solutions like those listed in HIPAA Eligible Twilio Services demonstrate how AI and automation are becoming integral for secure healthcare communication.
5G, IoT, and Next-Gen Connectivity
The rollout of 5G networks is accelerating the adoption of hipaa compliant voip in healthcare. Faster speeds and lower latency support clear, reliable voice communication even during peak usage. As hospitals and clinics deploy more IoT medical devices, integrating secure voice channels becomes essential.
These advancements introduce new risks, such as increased attack surfaces and more endpoints to protect. Healthcare IT teams must implement robust encryption, network segmentation, and device authentication to ensure all connected devices remain compliant.
A growing number of hipaa compliant voip providers are offering solutions tailored for 5G and IoT environments. By leveraging secure protocols and advanced monitoring tools, organizations can embrace next-gen connectivity while minimizing threats to sensitive patient data.
Regulatory Changes and Global Compliance
Regulatory expectations for hipaa compliant voip are evolving quickly. In 2025, healthcare organizations must stay updated on new HIPAA rules, especially regarding telehealth and remote communication. Cross-border data sharing is now subject to stricter controls, with GDPR and other international regulations influencing compliance strategies.
The Department of Health and Human Services regularly publishes updates and enforcement actions. Refer to the HHS Guidance on Audio-Only Telehealth for the latest official recommendations on using VoIP and other audio technology in healthcare settings.
Preparing for these changes involves ongoing risk assessments, updating business associate agreements, and ensuring all communication solutions align with both domestic and international standards.
Building a Culture of Security in Healthcare Communication
Future-proofing hipaa compliant voip requires more than technology; it demands a culture of security. Leadership must prioritize secure communication and invest in continuous staff training. Ongoing awareness programs help clinicians and support staff recognize potential threats and respond effectively.
Encouraging transparent incident reporting and rapid response to breaches is vital. Healthcare organizations known for strong security cultures often conduct regular drills and reward proactive behavior, setting a standard for others to follow.
Ultimately, the future of hipaa compliant voip depends on a shared commitment to safeguarding patient privacy at every level.As we've explored, choosing a HIPAA compliant VoIP system in 2025 is about more than just ticking regulatory boxes - it's about building trust, safeguarding patient data, and enabling seamless global communication. If you're ready to put these best practices into action and want a reliable partner with proven global reach, real time analytics, and dedicated developer support, you don't have to wait. Let’s take the next step together toward secure, compliant healthcare communications. Start now!